Terragrunt secrets management with Doppler

Why Terragrunt and Doppler
With Infrastructure as Code, you may find yourself facing a circular dependency loop when it comes to secrets. Some services you self-host to help manage business applications won't exist before you create the infrastructure. So you need a place for infrastructure secrets.
Thankfully there are lots of options. We can use encrypted files, either within versional control or saved somewhere externally. There are managed solutions such as HCP Vault or AWS Secrets Manager.
It was clear to see that Doppler is a great utility for developers to share secrets. But it's not a stretch to realise that Doppler can work for infrastructure secrets too.
In this article, I share the few steps required to get Doppler working with Terragrunt.
Managing secrets with Terragrunt
Terragrunt proposes 3 ways of managing secrets.
Environment variables
Encrypted files
Secret stores
With Doppler, we can combine the simple use of Environment variables with a secret store.
Using environment variables with Doppler
Step 1: Defining the environment variable within our Terragrunt file
In the example Terragrunt file, we've decided to use an environment variable to prefix our bucket name. In a real-world example, you may have secrets or local variables that you don't want inside version control.
Reference your variable within a terragrunt.hcl by using the get_env function:
remote_state {
# ...
config = {
bucket = "${get_env("TG_BUCKET_PREFIX", "")}-infrastructure"
key = "terraform/${path_relative_to_include()}/terraform.tfstate"
region = "${local.global.bucket_region}"
encrypt = true
}
}
Step 2. Adding the environment variable to Doppler
Once logged into Doppler, you can select a project, then the project environment (eg. production) and add your environment variable there.
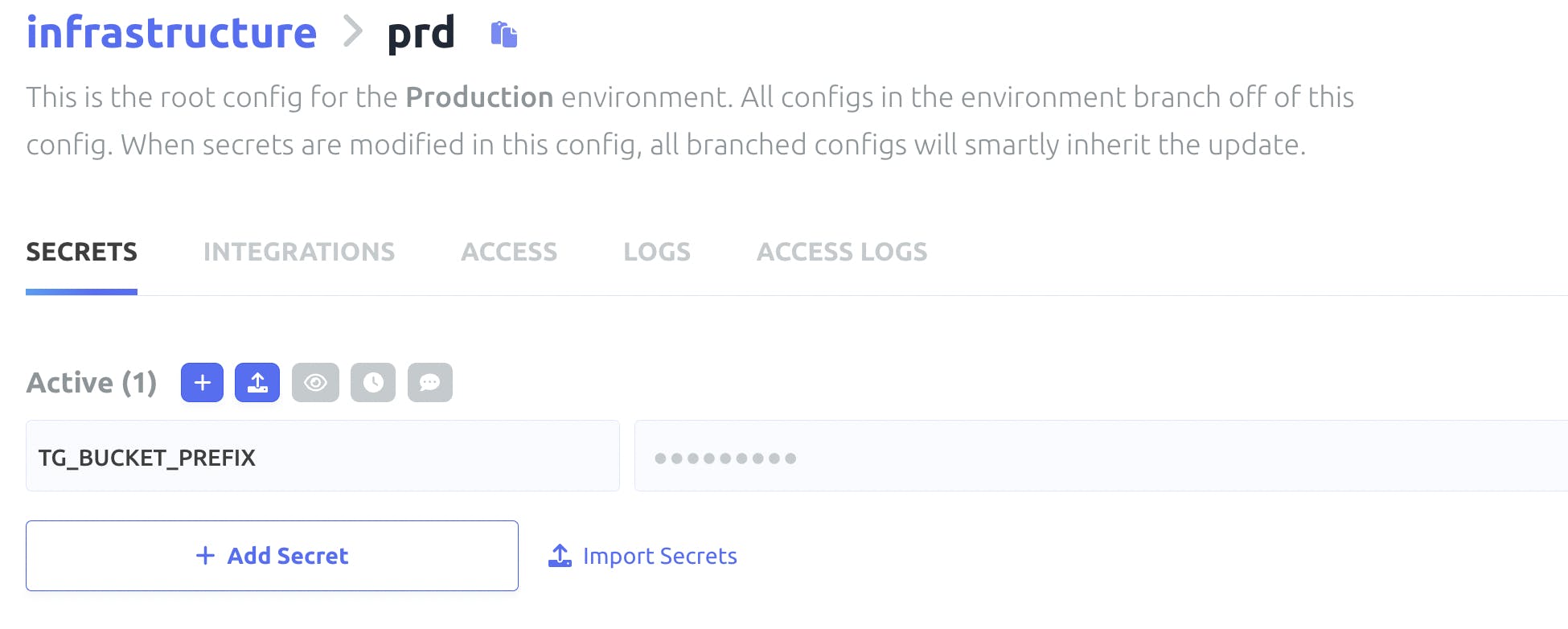
Step 3. Configuring Doppler on your Terragrunt project
To be able to use Doppler within your project, you must first set up Doppler to connect it to the right project and environment.
Run the setup command and select a project:
doppler setup
# > Select a project: [Use arrows to move, type to filter]
Select an environment (eg. production).
# > Select a config: [Use arrows to move, type to filter]
Once done, you can view the secrets from Doppler by running:
doppler secrets
Step 4. Injecting Doppler environment variables into Terragrunt commands
Finally, to run Terragrunt and inject secrets, we need to prefix the Terragrunt command with the Doppler run command.
doppler run -- terragrunt run-all plan
Finished
In conclusion, using Doppler for Terragrunt secrets management is a powerful and effective way to ensure that your infrastructure as code is secure, well-protected and straightforward to use.
Next steps
- How to get started with Doppler.
